Azure AD Configuration
SIFF Configuration
- Navigate to Admin > Organizations
- Edit the organization to use Azure AD
- Select the External Auth tab
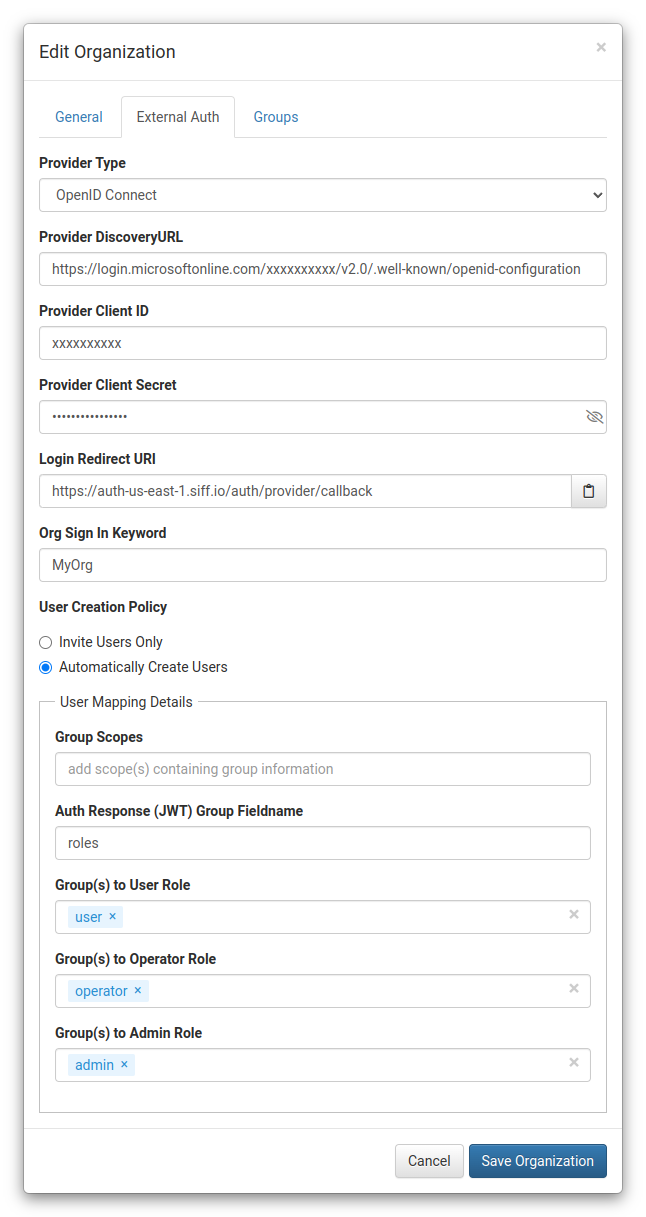
- Configure the fields as shown below:
- Provider Type:
OpenID Connect - Provider DiscoveryURL: set to the value from Azure AD > App Registration > Overview > Endpoints - OpenID Connect metadata document (endpoint)
- Provider Client ID: set to the value from Azure AD > App Registration > Overview - Application (client) ID
- Provider Client Secret: set to the value from Azure AD > App Registration > Certificates & secrets - secret value (NOT Secret ID)
- Org Sign In Keyword: use a unique keyword (e.g. your org name) to provide on the SIFF login screen to be redirected to your Azure SSO Login
- User Creation Policy: Automatically Create Users
- Group Scopes: leave blank
- Auth Response (JWT) Group Fieldname:
roles - Group(s) to User Role:
user - Group(s) to Operator Role:
operator - Group(s) to Admin Role:
admin
- Provider Type:
Azure AD Configuration
- Navigate to Azure AD > App Registration
- Select New Registration
- Name:
SIFF Client - Select the desired account type
- Under Resirect URI (optional)
- Platform:
web - URL: this should match the Login Redirect URI from the SIFF
Configuration, for the default region:
https://auth-us-east-1.siff.io/auth/provider/callback
- Platform:
- Name:
- Navigate to Azure AD > App Registration > SIFF Client > Overview. This provides values required for the SIFF Configuration above. Select Endpoints to see the URL for the OpenID Connect metadata document.
- Navigate to Azure AD > App Registration > SIFF Client > Authentication. Select the tokens for authorization endpoint - set ID tokens (used for implicit and hybrid flows)
- Navigate to Azure AD > App Registration > SIFF Client > Certificates & secrets
- Create New client secret
- Copy the Secret value and use that value in the SIFF Configuration above.
- Navigate to Azure AD > App Registration > SIFF Client > API permissions
(optional) Select “Grant admin consent” to pre-authorize SSO grant. - Navigate to Azure AD > App Registration > SIFF Client > App Roles
- Create three app roles as follows:
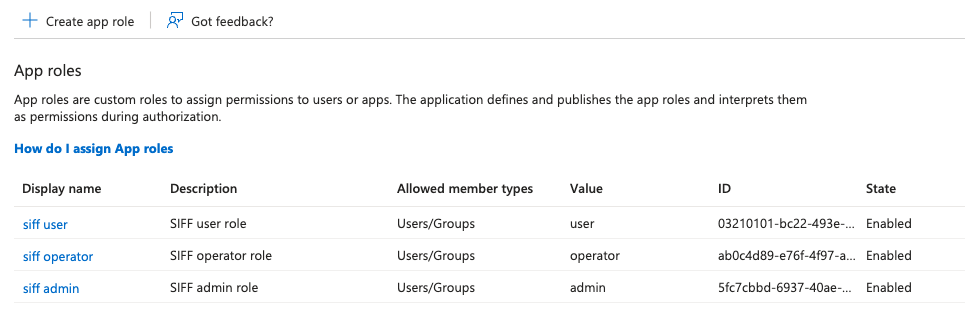
- Create three app roles as follows:
- Navigate to Azure AD > Enterprise Apps > SIFF Client > Users and Groups
- Add User / Group to the SIFF Client app
- Select Edit Assignment to assign app roles to users / groups
SIFF Login
On the SIFF Login page enter the Org Sign In Keyword from the SIFF Configuration above. This will redirect you to Azure SSO sign-in and then back to SIFF.