Access Credentials
Access Credentials are required in order for device discovery, service discovery, and monitoring to work. SIFF supports a number of different options:
- Username and Password: Used when connecting to a device with remote shell via SSH or Telnet.
- SSH Key (recommended): Used when connecting to a device using private keys via SSH.
- Agent / Collector: If a Collector or Agent is installed on a device then access is implied, however additional credentials may be required for privileged access.
Security Implications
In order to gather configuration information SIFF must be able to
read relevant file metadata and contents, along with executing commands.
This can either be done as the remote access user (or Collector/Agent
user), or by using elevated privileges with sudo on Linux/UNIX systems,
running as an Administrator on Windows systems, or executing a privilege
command on network devices.
Note that elevated privileges are only used if 1) privileged access details are provided as part of the Access Credentials, and 2) the Service Definition actually requires elevated privileges.
Note: It is optional to provide elevated privilege access details. If not provided then collection will still be attempted as the regular user.
Note: Some devices may limit the number of incorrect login attempts in a given time window. If so then make sure the correct credentials are attempted first - see Access Ordering below.
Creating Access Credentials
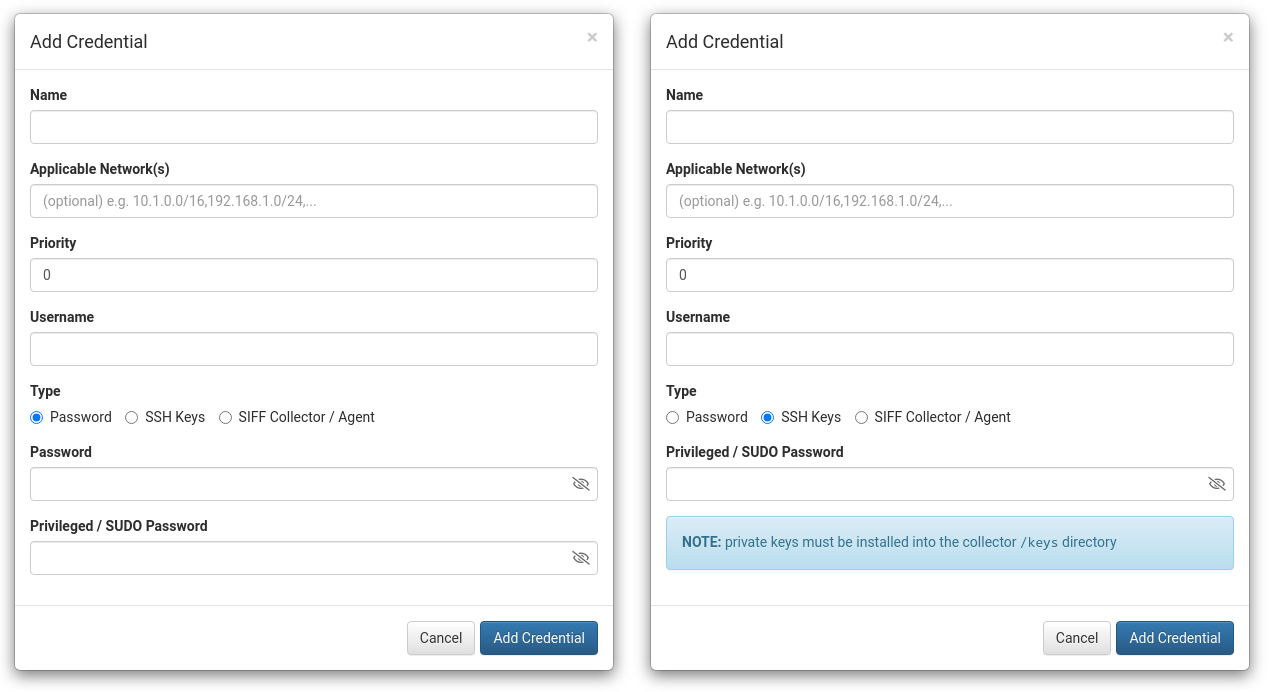
| Field | Description |
|---|---|
| Name | Required. Arbitrary name used to identify this Access Credential. |
| Applicable Network(s) | Optional. If left empty this credential will apply to all Networks. Otherwise specify a comma separated list of network/mask to restrict usage to specific networks. For example: 192.168.1.0/24,10.0.0.0/24 |
| Priority | Optional (default to 0). Multiple Access Credentials may apply for a given device and Priority is used to order the credentials when attempting to manage a device for the first time, or when access is lost to an existing managed device. |
| Username | Required. The username used when connecting with SSH or Telnet. For the Agent / Collector Type this credential will apply if the username matches the user the Agent or Collector is running as (by default siff). |
| Type | Required. Sets the type of access credential. NOTE: when using SSH keys see below for more information. |
| Password | Required for Password Type, not shown for other Types. This is the password used for remote access. |
| Privileged / SUDO Password | Optional. See Security Implications above for more information. |
Access Ordering
If multiple credentials apply for a given element then the following rules will apply:
- If the element is already managed, use existing credential
- If this is a new element, or authentication failed then generate a
list of applicable credentials:
- filter by Applicable Network - only relevant credentials are considered
- order by Priority
- order by Applicable Network CIDR size (smaller network = higher priority as it is more specific)
- order by Type: SSH Keys -> Password -> SIFF Collection/Agent
- finally order by popularity (most used credentials first)
Note: To force an existing element to retry the list of applicable credentials then Unmanage and re-Manage the element.
Using SSH Keys
When using SSH Key type credentials the Collectors that need to use these credentials must have the private keys installed. These are installed on the Collector system itself and are never shared with SIFF.
If existing private key(s) are to be used then skip to the install steps below.
To create a new private key:
- Use
ssh-keygenor equivalent such as PuTTYgen for Windows to generate a new key pair. i.e. a private and public key. For example:ssh-keygen -f ~/.ssh/siff-collector - The Collector only needs the private key, from the example this would
be
~/.ssh/siff-collector. - Hosts where the Collector requires access would need to have the
public key (
~/.ssh/siff-collector.pub) installed. This will depend on the target device but for OpenSSH based systems thessh-copy-idutility could be used or manually installed into~/.ssh/authorized_keys
To install a private key:
- Stop the Collector
- Copy the private key to
/opt/siff/keysfor Linux/UNIX based systems and toC:\Program Files\siff\keysfor Windows based systems. - (optional) If the private key is passphrase protected then register
the passphrase with the collector by running:
collector --setkeypass key/<priv_key_filename>. - Restart the Collector
- Repeat for other Collectors that also need the private key
Note: Only place private keys in the keys directory or the
Collector will fail to start. If the Collector is missing
passphrases it will also fail to start.